How to get more detail of worked or failed login attempts
They say as a Unix Administrator you will never know everything… how true that is. Todays simple post shows you how you can get more detail from your btmp, wtmp, and utmp files.
One of the core roles of any Unix Administrator is looking after the security of your servers. That ranges from maintaining your firewall, forcing users to reset their passwords regularly, or analysis of your servers to make sure you are aware of any intrusions that occur that you should be aware of.
This is for all those Unix Admins who have (like me) been using ‘strings’ to get any information about both worked or failed login attempts to your server. If you have not used strings before then I advise you dont, and read the rest of this post and use utmpdump instead!!!
The problem with using ‘strings’ is that you dont know WHEN an attempt happened. A timestamp is what you really need to know if you want to report abuse to cloud hosting companies like AWS or even private hosting companies of people trying to hack into your server.
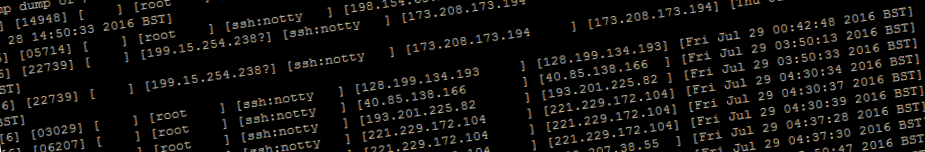
So I did some digging and found a very useful command called utmpdump.
On CentOS 6 this is installed as default (even on a minimal install it seems), but if it is not there for you then you will find it in the sysvinit-tools package you can install like this –
yum install sysvinit-tools
Then to view the info utmpdump can give you just use the command like this.
For failed login attempts –
utmpdump /var/log/btmp
For successful login attempts –
utmpdump /var/log/wtmp
For currently open sessions –
utmpdump /var/run/utmp
The output from the above gives you all the details (date/time, timezone, ip address/hostname, username) that you could possibly want or need to get those damn hackers off your system!
Enjoy!